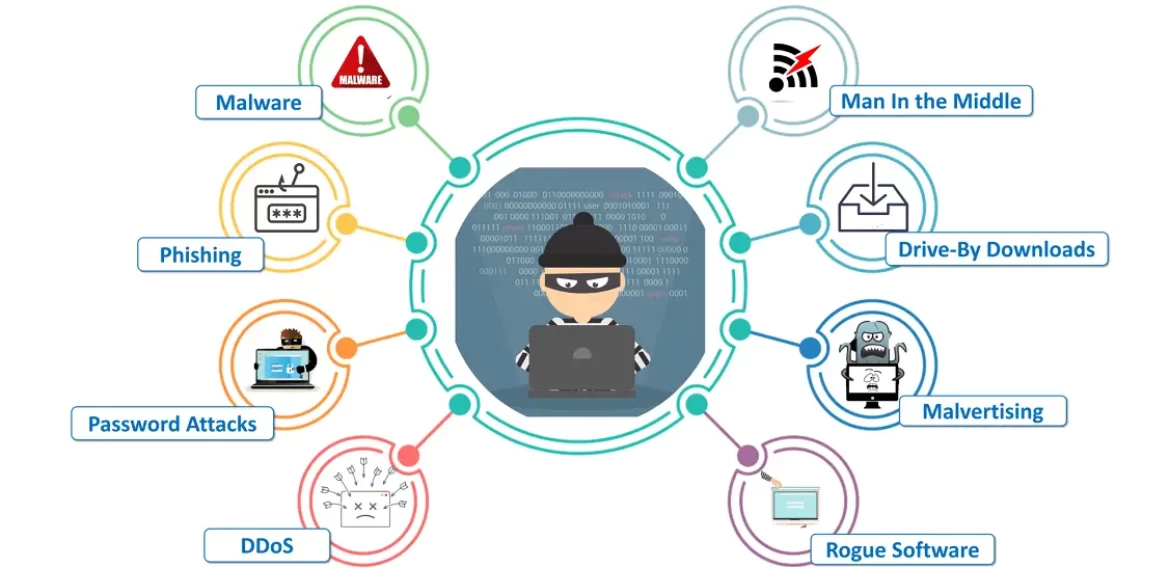
TYPES OF CYBERCRIME
Today, cyberspace is the most apt platform for cybercriminals to carry out their operations. With the introduction of the internet at every level of the workplace, offices have developed a vulnerability that can be easily exploited by online miscreants. Even the common man has not been spared by such entities. Reports of hack attacks on individuals surface every day on print as well as the digital media.
Precaution is better than cure holds true in the present scenario. Preventing such attacks from happening is the best measure one can resort to. And the first measure towards preventing such attacks from happening is knowing about the different types of cyber-attacks. So, keep reading to find out the various kinds of cyber-attacks.
1 Malware Attacks
Malware is blanket-term which includes various threats like viruses, worms, Trojans, etc. These are the self-executing codes designed to harm the victim’s system. Malware is introduced into the victim’s computer using different means like email attachments, download from malicious sites, and in some cases even through infected flash/pen drives. Once attached, they pry on the system’s vulnerabilities to further deteriorate the system’s condition.
2 Phishing Scams
One of the oldest tricks in the book for cyber-criminals. In this case, a malicious link is sent to the target’s email. Upon clicking, it directs the target to a phishing site (aesthetically similar to your email or social network site) where the target is required to put in his sensitive credentials. The credentials put in are then accessible to the hackers, and they may use them to their benefit.
3 Password Attacks
These attacks are targeted towards getting access to the victim’s passwords. The hackers employ different techniques like brute force attacks, or running malicious codes, or using dictionary attacks to retrieve the victim’s passwords. In the case of success of any of these methods, the password comes into the hands of cyber-criminals. Using a strong password and changing passwords at regular intervals seems to be the only defense against such attacks.
4 DoS Attacks
Another type of cyber-attack used mainly against the corporates is the Denial of Services (DoS) attack. This method uses transmitting a huge volume of traffic onto the victim’s network, thereby disrupting the service by overloading it. An even more dangerous attack is the DDoS (Distributed-Denial-of-Services) attack, where multiple computers are used to disrupt the services on similar lines.
5 Malicious Advertising
Ads are rampant on the internet. Malicious codes are inserted in such ads, which are downloaded to your system upon clicking. These ads are put on prominent sections on a web page prompting the users to click on these ads. Such ads may even be present on popular or legitimate sites where the users are completely unaware of the dangers that they lie.
6 Man-in-the-Middle (MITM) Attack
As the name says, a ‘man’ is present in between the endpoints, and hence, any information entered by the victims is available to these entities. Usually, present on transnational and business sites, the “man” can snoop all your information and use it to their advantage. They may even impersonate your banking sites and prompt you to fill in your sensitive data.
7 Drive-By Downloads
You may be surprised to know that malicious code may be inserted into your system even by just visiting a website. A minute code is inserted into the victim’s computer, which uses another computer to download the rest of its components. The code then uses the system’s or other programs (like Java, Flash) vulnerabilities to execute further.